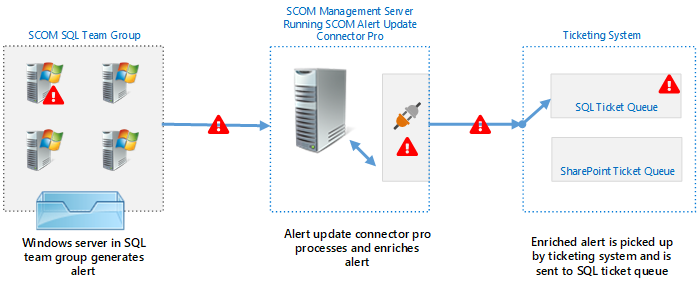
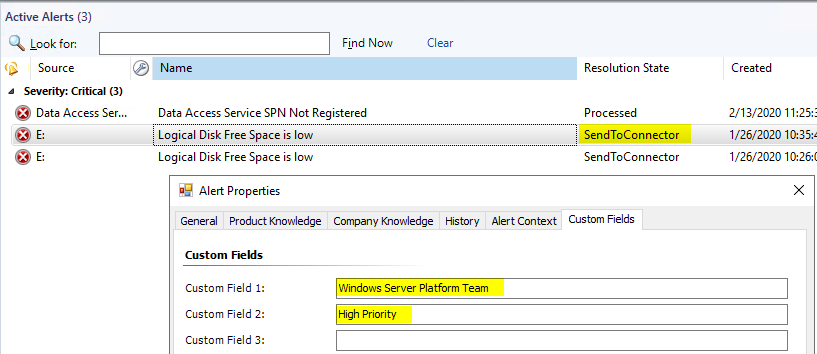
First I need to create a Azure Virtual Network and Subnet. I go to All services  and find Virtual networks
and find Virtual networks
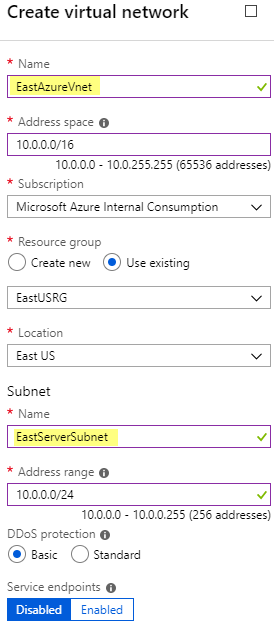
I add a Virtual network called EastAzureVnet with a Subnet called EastServerSubnet and leave the defaults. (Make sure this address space doesn’t overlap with your on-prem network)
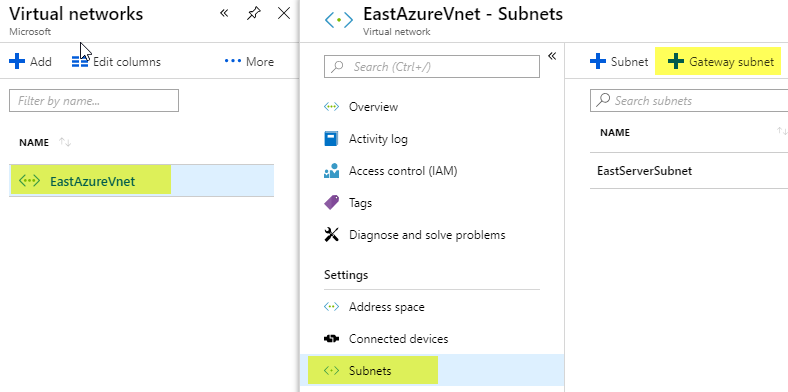
Now I open my Virtual network I just created called EastAzureVnet and click Subnets and click Gateway subnet
Leave the defaults and click OK
Virtual Network Gateway
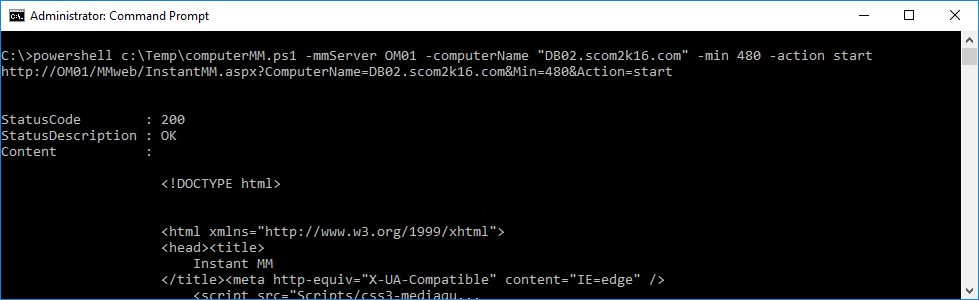
I need to create a Virtual Network Gateway. I go to All services and find Virtual network gateways
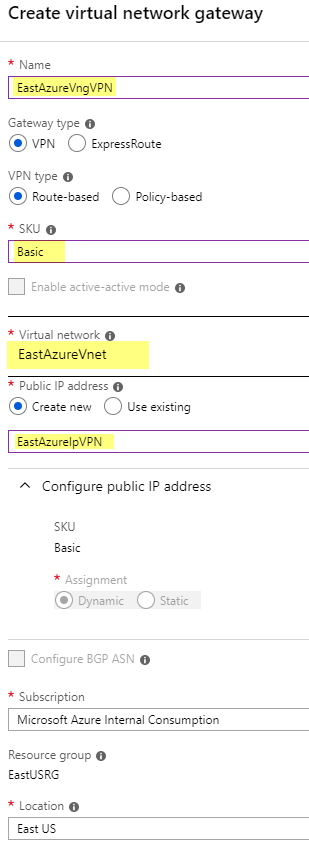
I set the following values and click Create. (Note: This will take about 15 minutes, so go have a  or a
or a  )
)
Name: EastAzureVngVPN
SKU: Basic (If this were for production I would choose VpnGw1 or higher)
Virtual network: EastAzureVnet
Public IP address: EastAzureIpVPN
Local network Gateway
Next we need to create a Local Network Gateway. I go to All services and find Local network gateways 
I use my on-prem network information.
My lab uses IP address range 192.168.2.1 – 192.168.2.255 (aka 192.168.2.0/24)
My Example External IP is 67.37.217.79
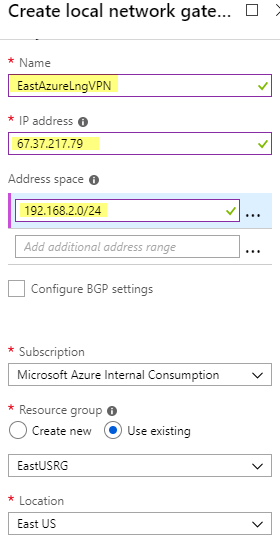
After it is created click on the Local Network Gateway called EastAzureLngVPN and click Connections, Then click Add
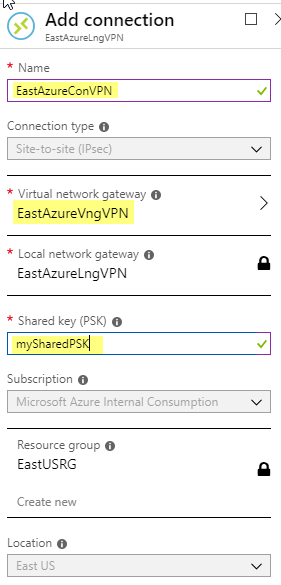
I use the following information and Click OK. Create and save your shared key as you will need this when setting up the PFSense side. (You will want your Shared key to be more complex then the example)
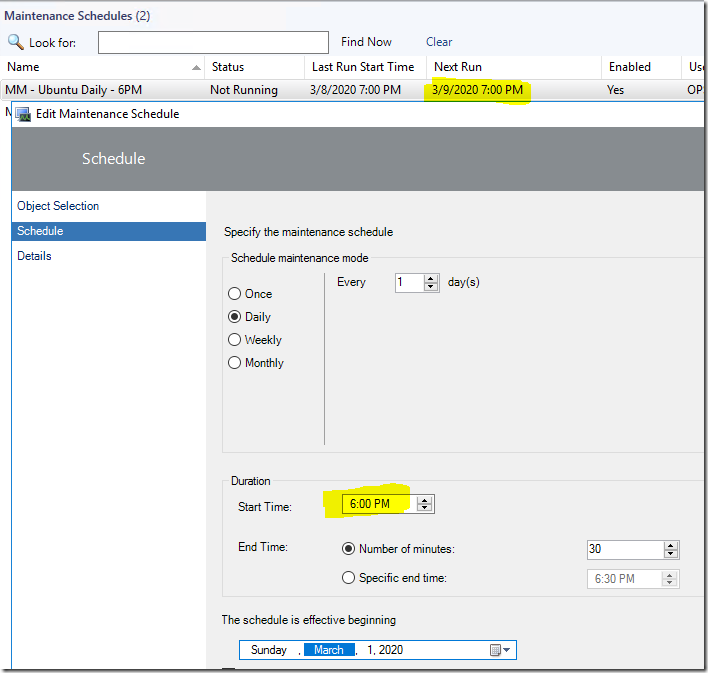
PFSense
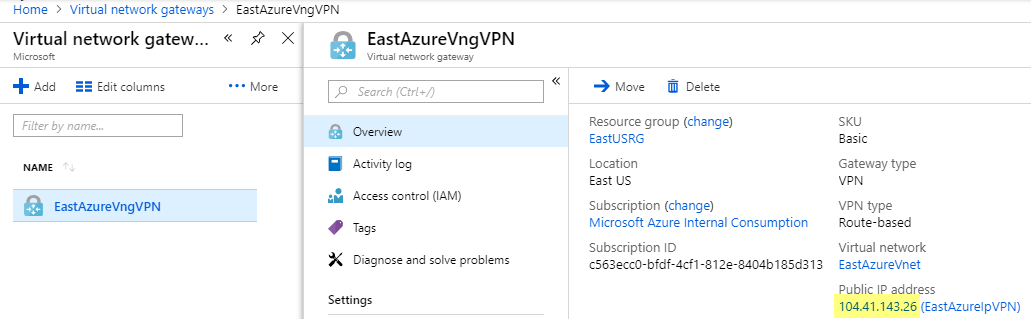
In Azure go back to Virtual Network Gateways and get your public IP Address for your Azure VPN
Next I go over to my On-Prem PFSense Firewall and click VPN, IPSec
Click Add P1, I changed the following settings
For Remote Gateway use your Public IP Address from your Azure Virtual Network Gateway
For Pre-Shared Key use your Pre-Shared Key
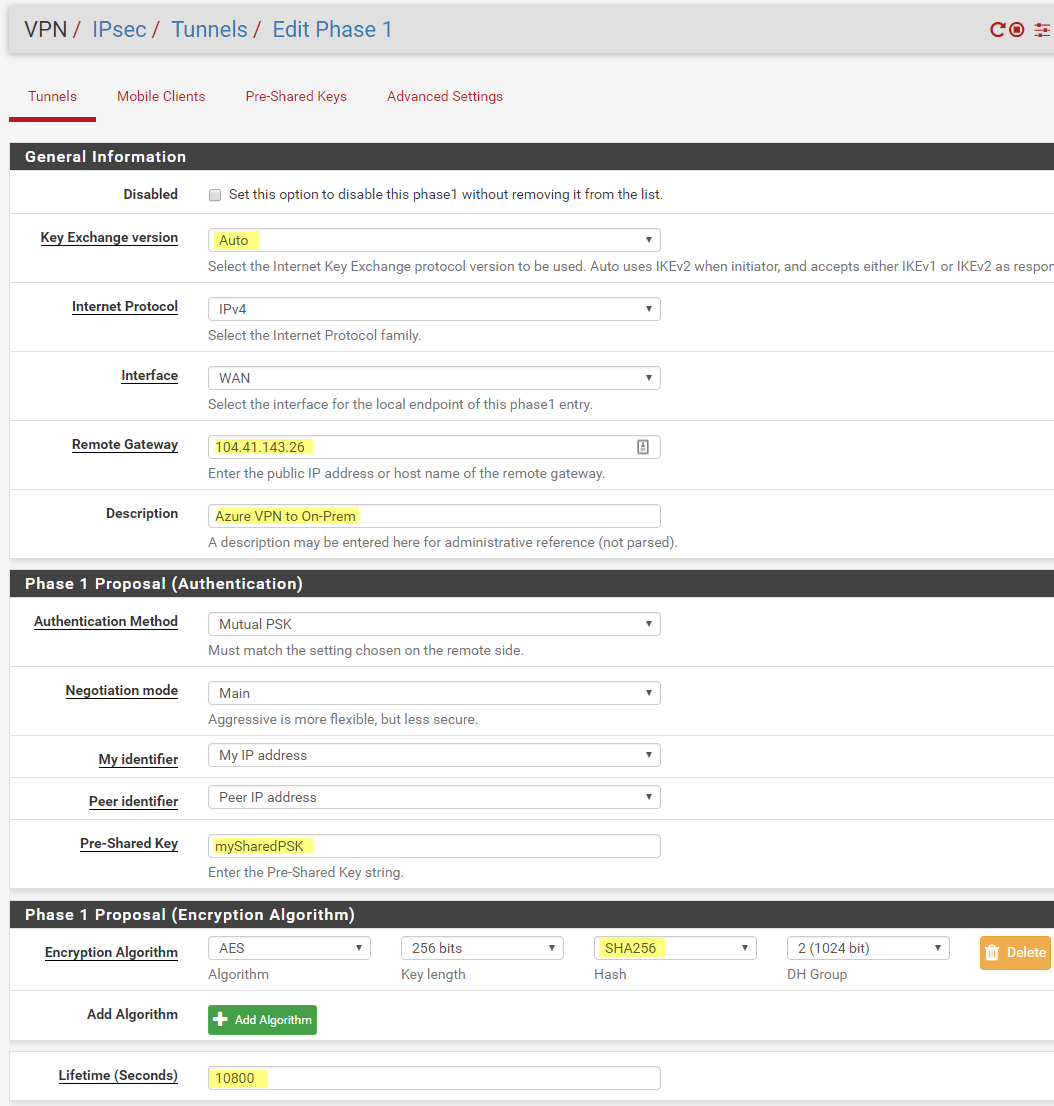
Click Save
Then Apply Changes

Now Click Show Phase 2 Entries, and click Add P2
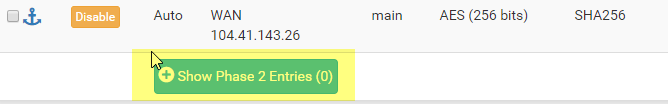
For P2 (Edit Phase 2). I go back to Azure to get the address space.
Set the Remote network address to the address space in Azure. (Not the Subnet)
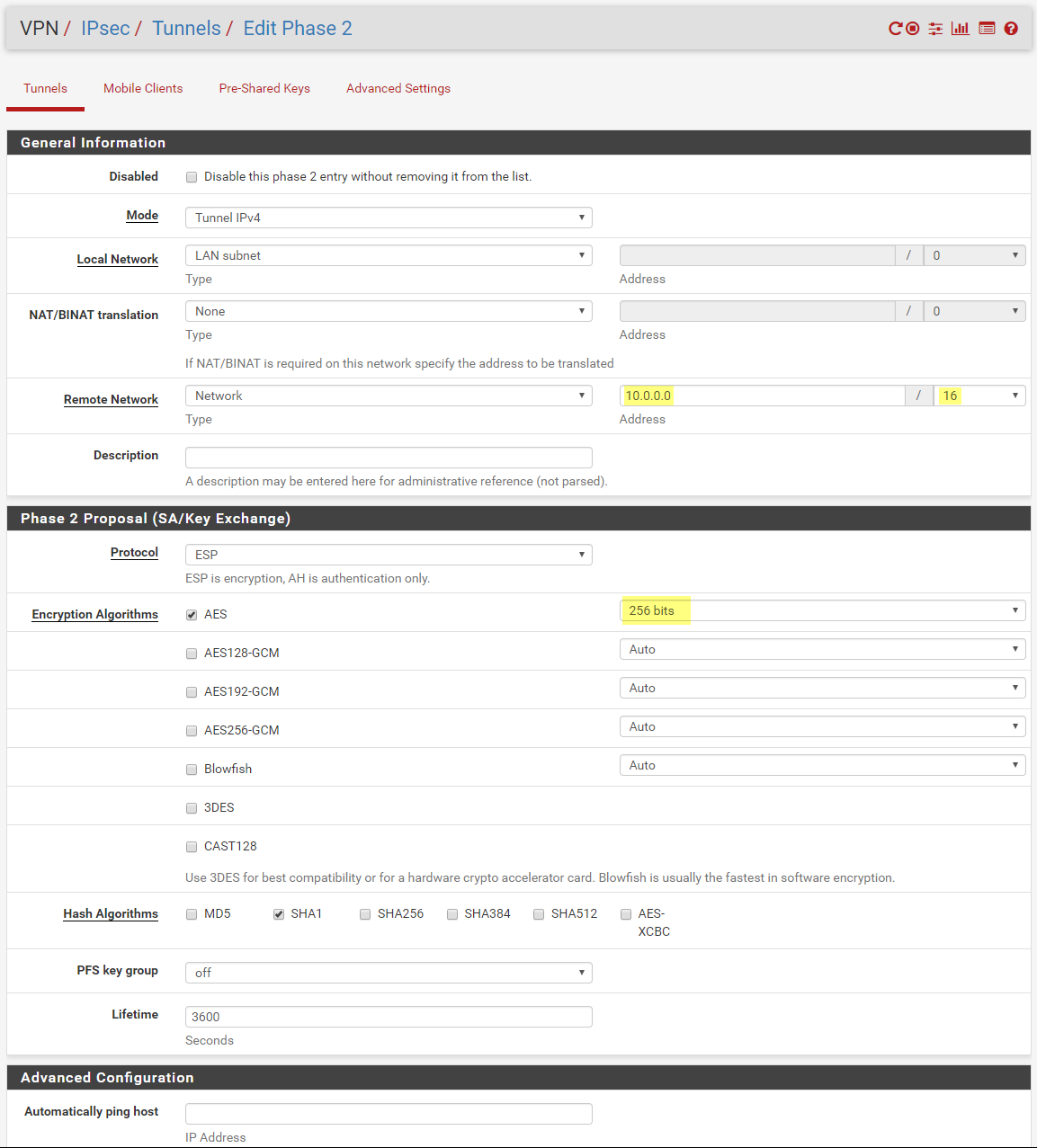
Click Save, and Apply Changes.
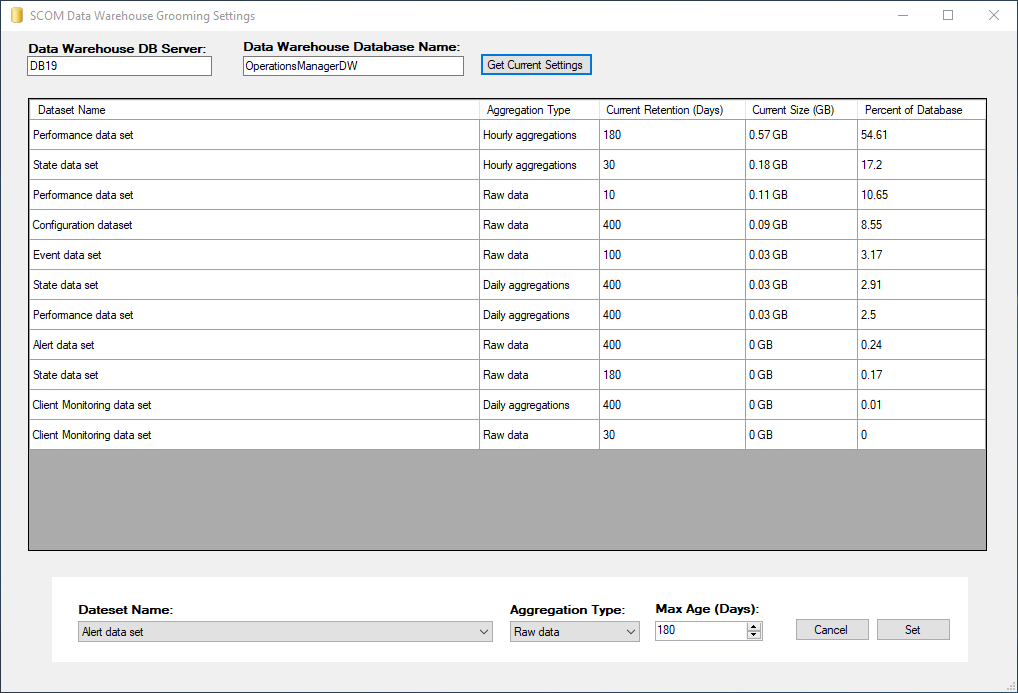
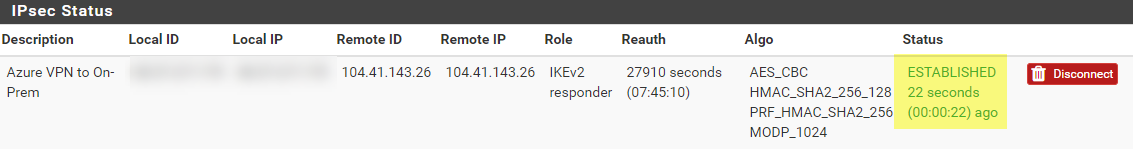
Now if we go to Status, IPsec
I can see we have Established a connection
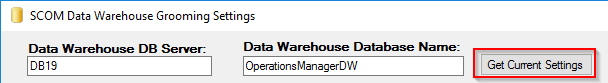
Lastly I need to create a firewall rule. I go to Firewall, Rules. The select IPsec and click Add
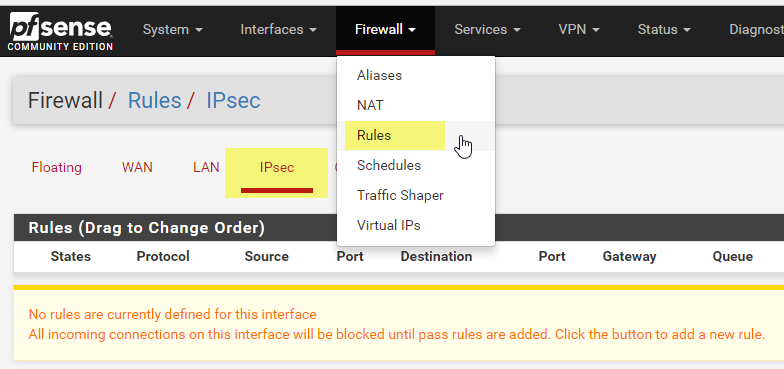
Change Protocol to Any. You can lock this rule down to suit your needs.
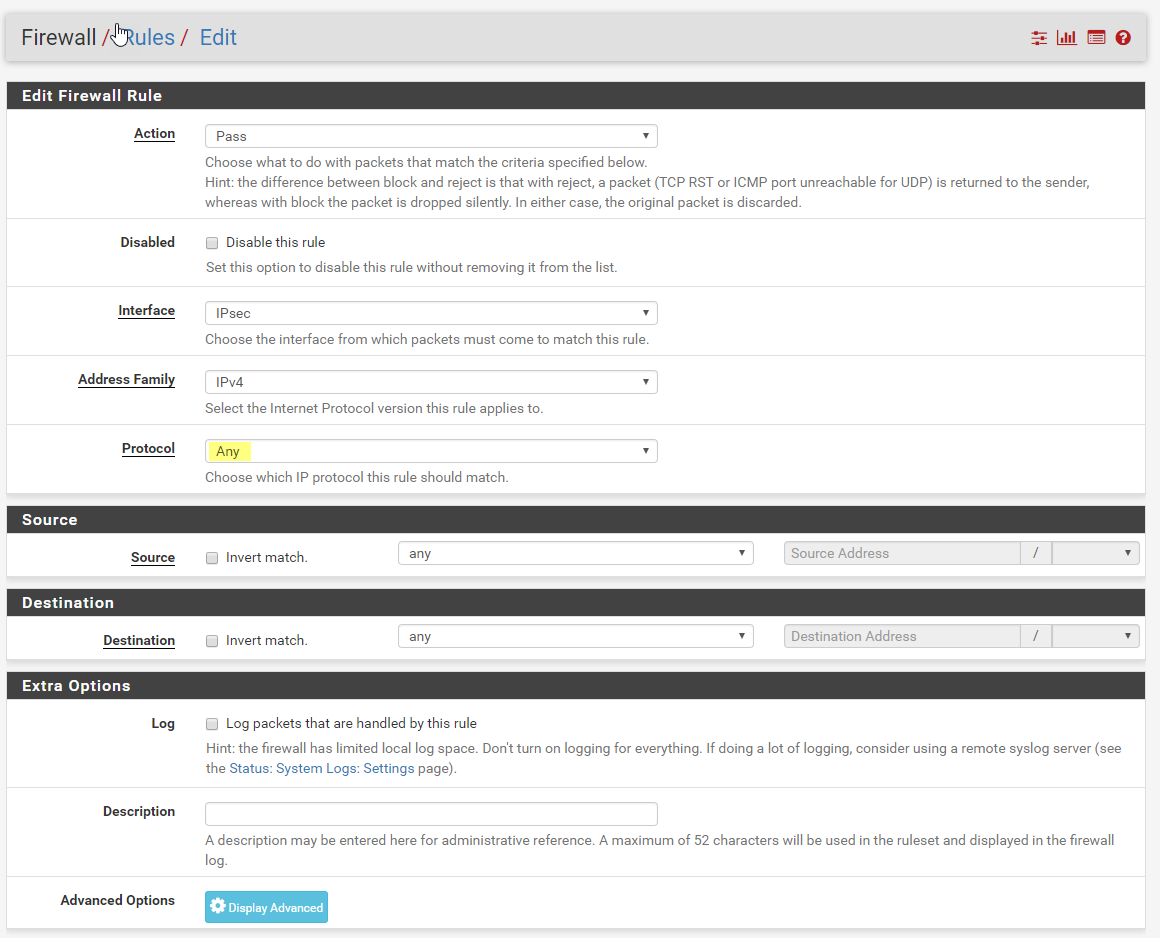
Click Save and Apply
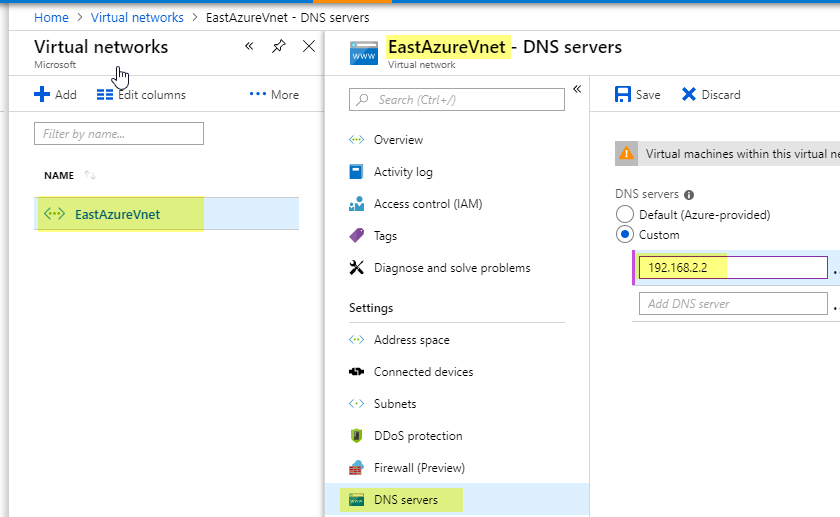
To get DNS working correctly. (So you can Add VMs to your Domain)
I set you DNS server for your Virtual Network to my local On-Prem DNS server.
One note. Azure blocks much of ICMP traffic. So to test, create a VM with a Public IP Address of None. Then connect with Remote desktop.

For general information on Azure Site-to-Site VPNs see https://docs.microsoft.com/en-us/azure/vpn-gateway/vpn-gateway-howto-site-to-site-resource-manager-portal